Install
There are many ways to install Catalyst. The following describes a reference architecture on an Ubuntu 22.04 server. Feel free to adapt it to your needs.
- Reference Architecture
- Reference Architecture with Load Balancer / Proxy
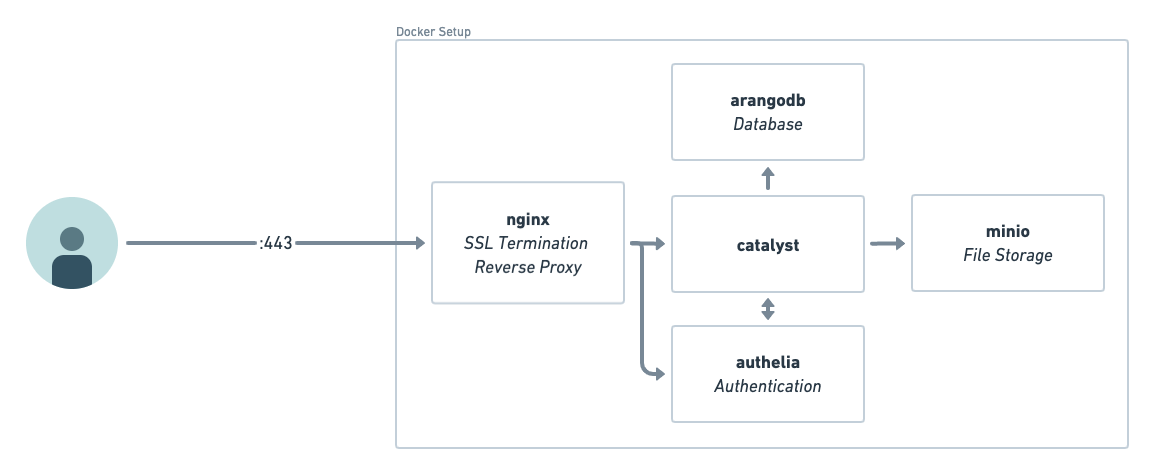
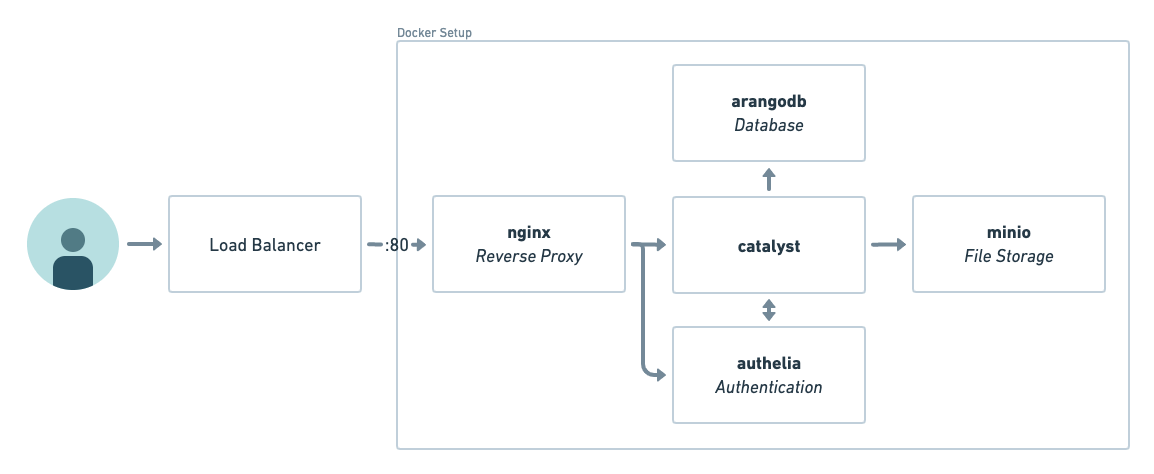
Installation Script
The installation script will create secrets and set up a docker compose deployment.
It is tested on Ubuntu 22.04 but should work on other Linux distributions and macOS as well.
Installation Process
- Set up 2 new (sub)domains, one for catalyst and one for authelia (OIDC user management).
- Set up the catalyst server.
- Set up a Ubuntu 22.04 server.
- Point the domains from step 1 to the server.
- Ensure Docker,
Docker Compose,
unzip,curl,openssl, andsedare installed. - Download the installation script:
curl -sL https://raw.githubusercontent.com/SecurityBrewery/catalyst-setup/v0.10.3/install_catalyst.sh -o install_catalyst.sh - Adapt the command to your needs:
bash install_catalyst.sh \
<hostname> \
<authelia_hostname> \
[<ssl_certificate> <ssl_certificate_key> | --no-ssl] \
<admin-user:admin-password:admin-email> \
<user:password:email> ...hostnameis the domain name of the catalyst server, e.g.https://try.catalyst-soar.comauthelia_hostnameis the domain name of the authelia server, e.g.https://authelia-try.catalyst-soar.comssl_certificateandssl_certificate_keyare the paths to the SSL certificate and key. If you handle ssl termination at a load balancer or reverse proxy, you can use--no-sslto disable SSL.admin-user:admin-password:admin-emailis the admin user that will be created.user:password:emailare the users that will be created. You can add as many users as you want, but also add them later.
- Run the command, e.g.:
bash install_catalyst.sh \
https://try.catalyst-soar.com \
https://authelia-try.catalyst-soar.com \
--no-ssl \
admin:admin:admin@example.com \
alice:alice:alice@example.com \
bob:bob:bob@example.com - Wait for the installation to finish. Catalyst will be available at
<hostname>. - Log in with the credentials from above.
Local Installation
Please acknowledge that this is for testing ONLY and NOT recommended for ANYTHING ELSE!
To run a test deployment of Catalyst on your local machine execute the following steps:
- Add the following lines to your
/etc/hosts:127.0.0.1 catalyst.localhost127.0.0.1 authelia.localhost
- Ensure Docker,
Docker Compose,
unzip,curl,openssl, andsedare installed. - Download the installation script:
curl -sL https://raw.githubusercontent.com/SecurityBrewery/catalyst-setup/v0.10.3/install_catalyst.sh -o install_catalyst.sh. - Generate a self-signed certificate:
openssl req -x509 -newkey rsa:4096 -sha256 -days 3650 -nodes -keyout example.key -out example.crt -subj "/CN=localhost". - Run the command, e.g.,:
bash install_catalyst.sh \
https://catalyst.localhost \
https://authelia.localhost \
/some/path/example.crt /some/path/example.key \
admin:admin:admin@example.com - Wait for the installation to finish. Catalyst will be available at
catalyst.localhost. - Log in with the
admincredentials from above. - Due to the self-signed certificates, you have to ignore the corresponding warning in your browser. You might face a
failed login after you ignored the certificate warning when being redirected to
authelia.localhost.In this case, navigate tocatalyst.localhostand login again.
User Management
Users are managed by Authelia.
The user_database.yml file is located at authelia/user_database.yml.
You can also use other OIDC providers like Keycloak.
Adjust the OIDC_* environment variables in the docker-compose.yml file and remove the authelia service if you want
to do that.
Self-Signed Certificates
If you want to use self-signed certificates and an external OIDC provider you might need to add them to the catalyst container, so that it trusts the connection to the OIDC provider.
…
catalyst:
volumes:
- "./mycert.crt:/etc/ssl/certs/mycert.crt:ro"
- "./myroot.crt:/etc/ssl/certs/myroot.crt:ro"
…